Eliminate Security Gaps with Mobile Vulnerability Management
As an integral component of Lookout Mobile Endpoint Security, our mobile vulnerability management (MVM) technology simplifies the challenge of combating software vulnerabilities, ensuring that your data is protected.


Making the impossible possible
Our MVM technology addresses the persistent concern of protecting your mobile fleet from vulnerabilities. We ensure that you have the visibility and control to embrace hybrid work without leaving gaps for attackers to exploit.
Automated data protection


Automated access control
Using AI-powered insights, we enable you to build policies that automatically limit access when a device has vulnerabilities that you deem unacceptable.

End-user remediation
With our in-app notifications system, we provide clear instructions to your users so they understand why they’ve lost access and how to resolve it.
An overview of MVM
Take a look at what MVM looks like when it tackles the complexity of mobile vulnerability, both from an administrator and end-user’s perspective.
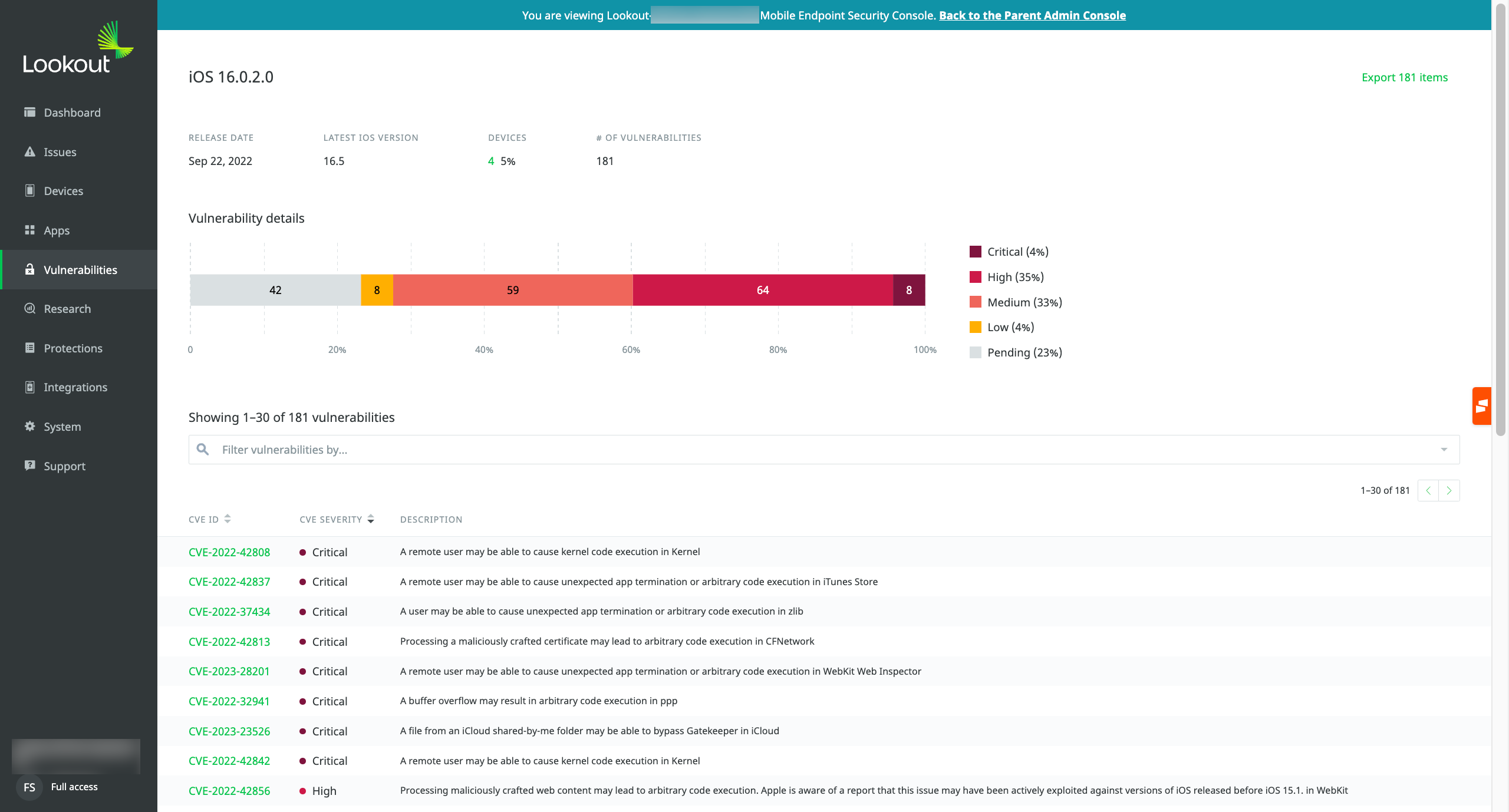
This is the view an administrator gets from the Lookout console for MVM. It provides a comprehensive overview of available OS versions and security patches for both managed and unmanaged mobile devices in your fleet.
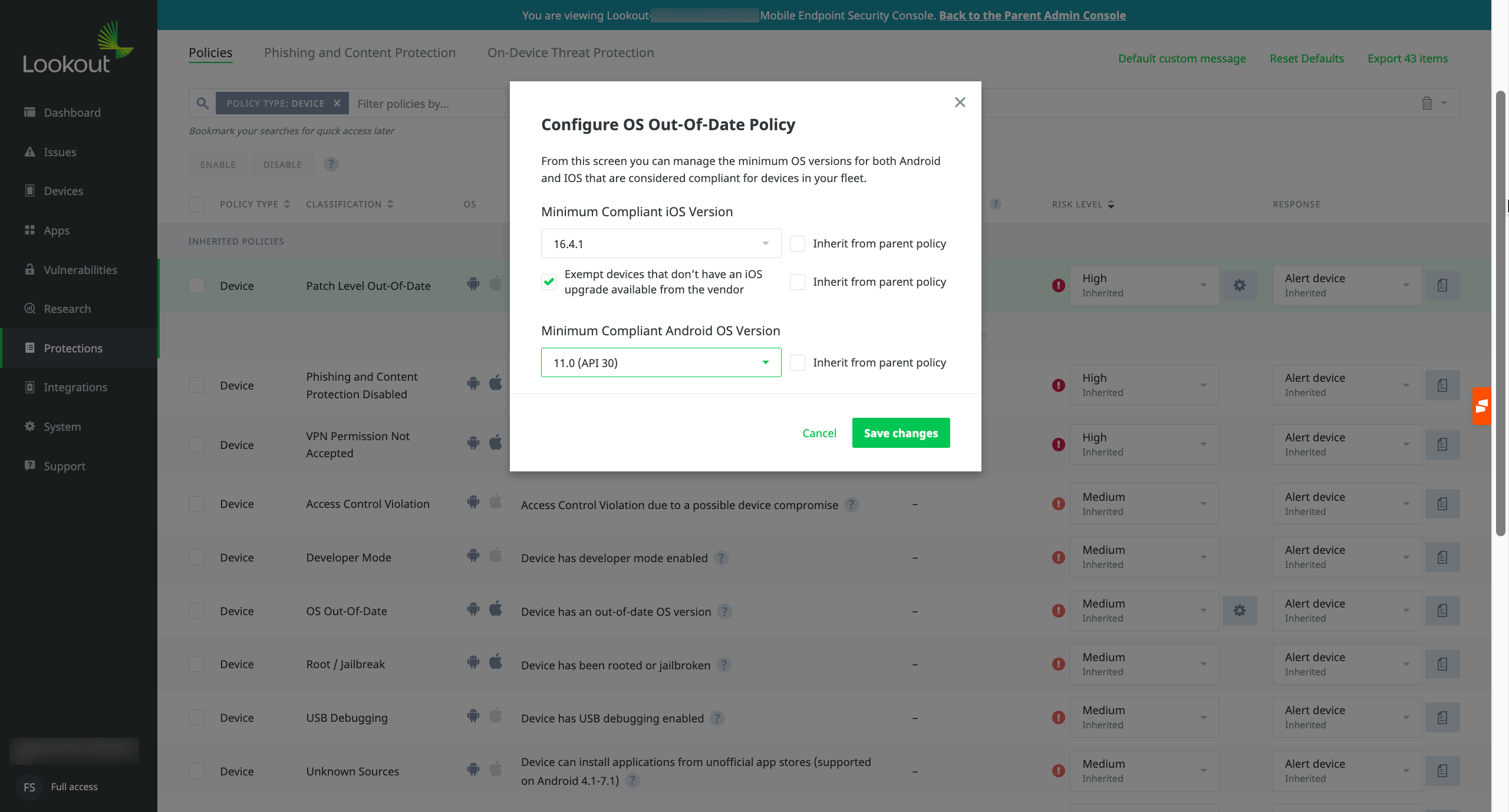
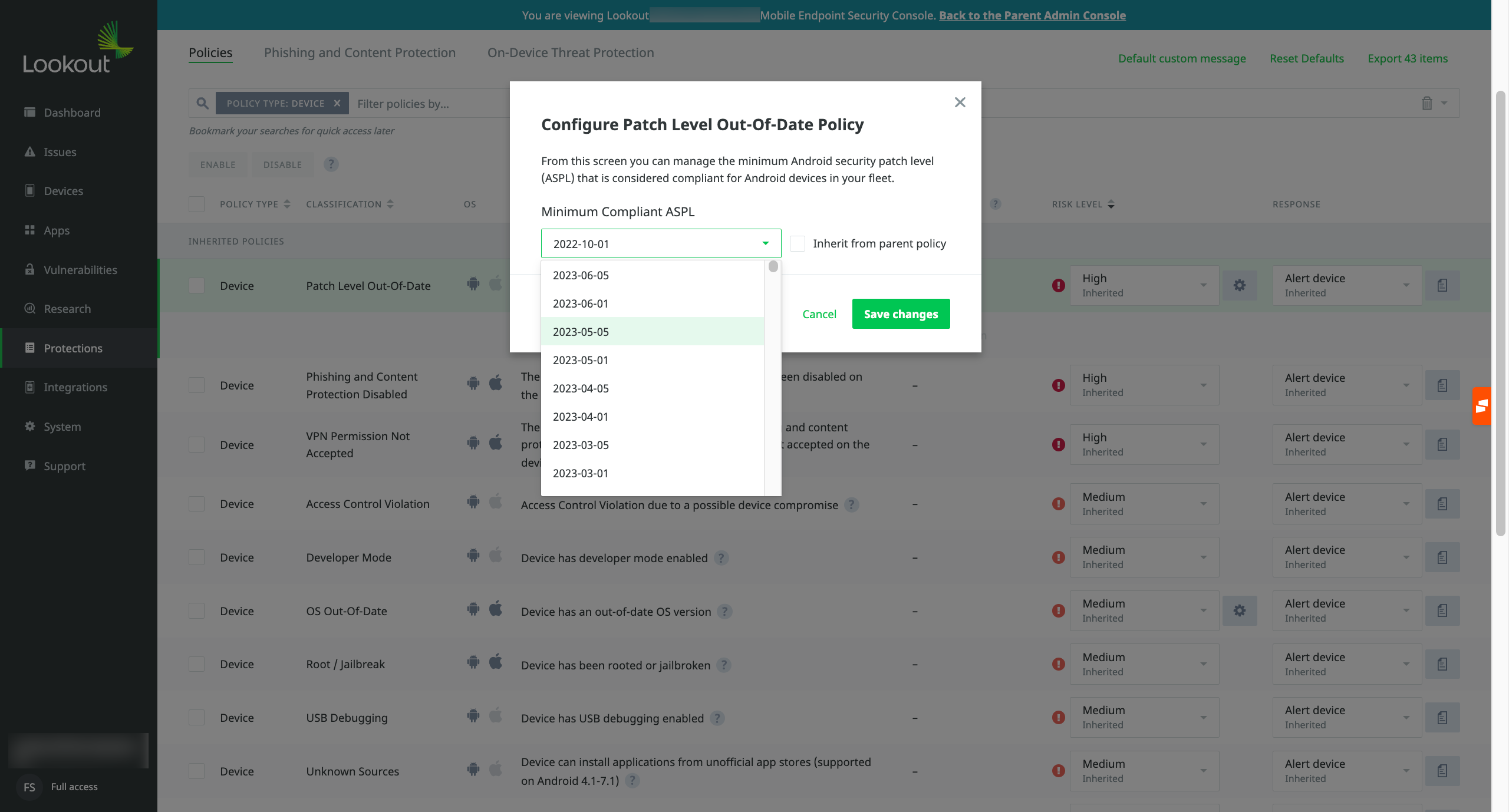
This is the interface an administrator encounters when configuring policies. It's designed to guide the administrator in establishing how security measures enforce operating system patch management.
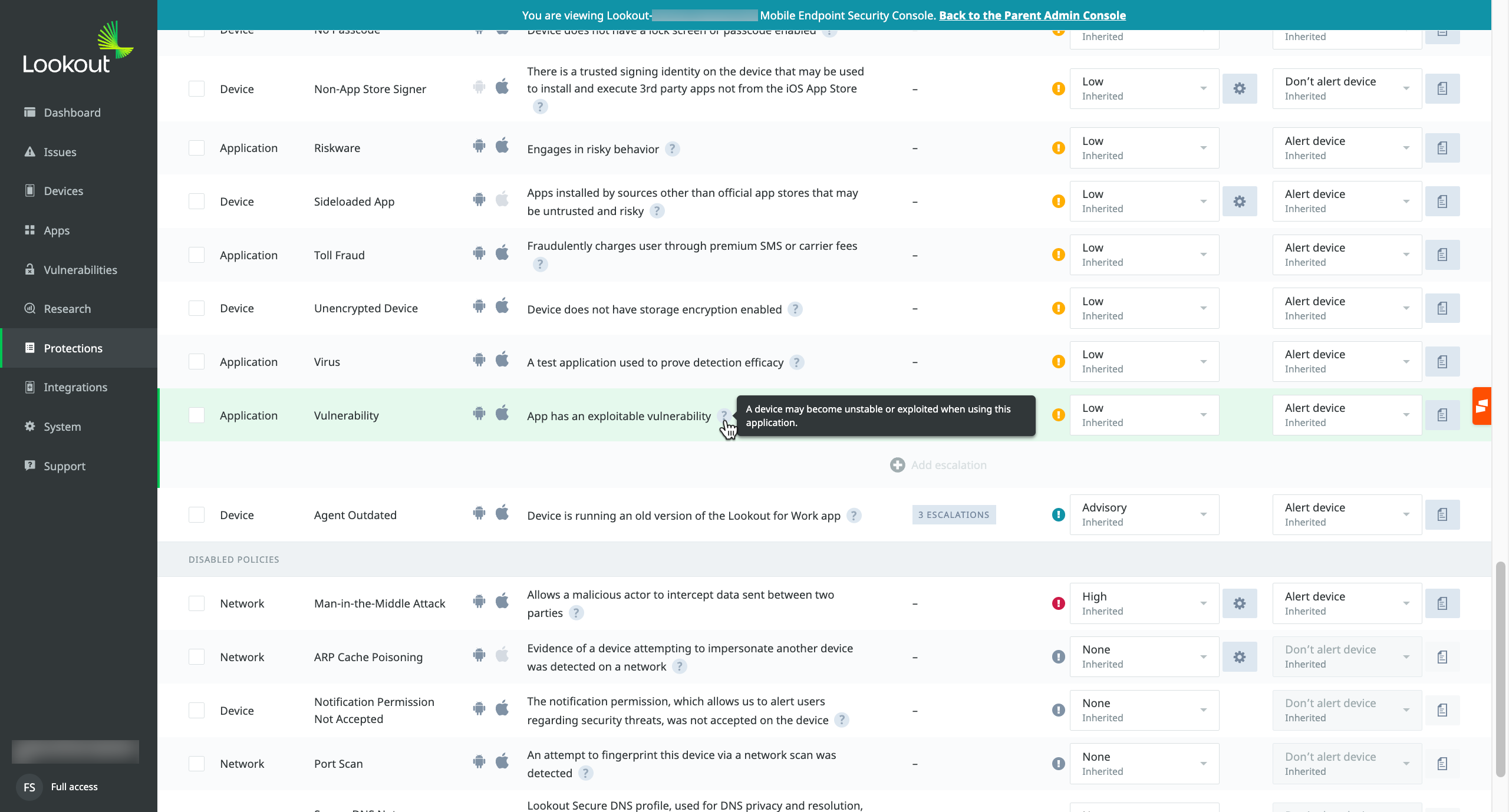
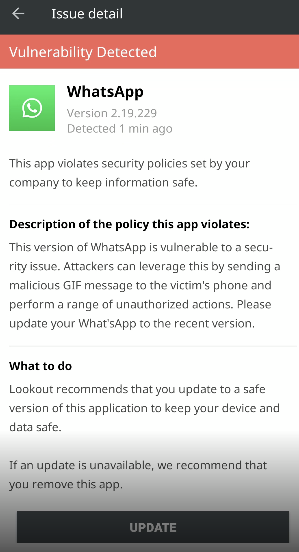
These views represent both the end-user and administrator perspectives. They illustrate how MVM identifies vulnerable apps on a device and the subsequent alerts sent to both the user and the security team.


















.png)

.webp)

