


December 11, 2025
The Dark Side of Going All-In on Microsoft Security
In the complex world of cybersecurity, the allure of simplicity can be very compelling. For many organizations navigating the digital landscape, Microsoft 365 offers a tempting option—an all-in-one suite of productivity, collaboration, cloud, and security tools. However, ease of use comes with hidden risks. Like any large platform, Microsoft 365 can be compromised, and history shows it has been a high-value target for attackers.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
#
results
#
filters applied


What Is a Large Language Model (LLM)?
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.
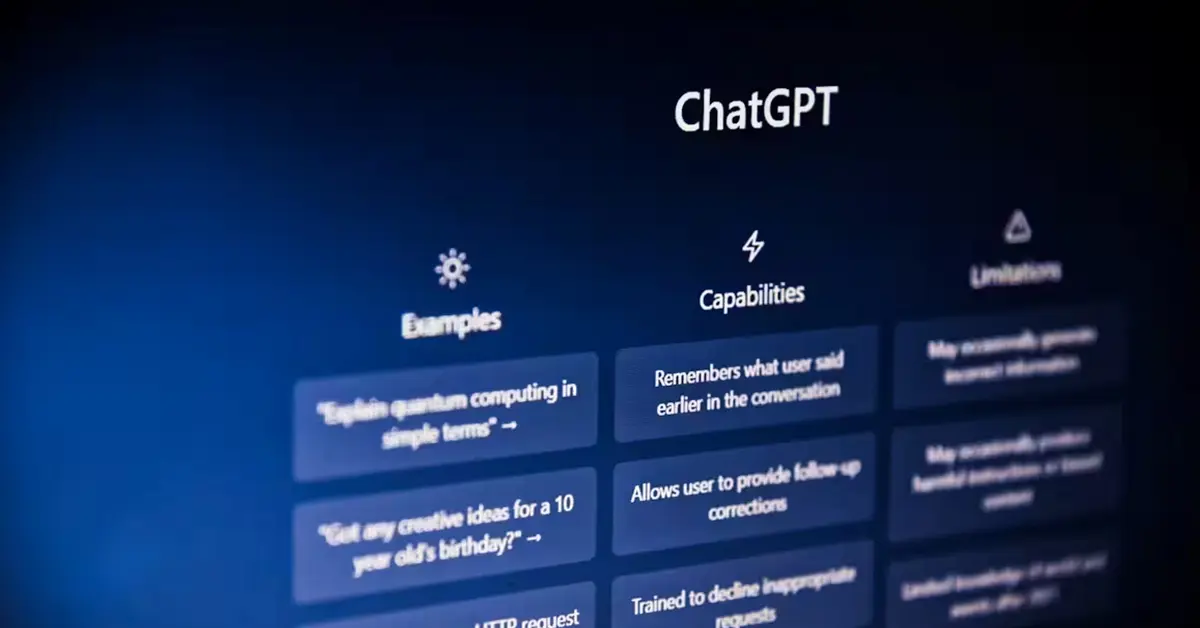

Prompt Injection: The Hidden Threat Hijacking Your LLMs (and How to Stop It)
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


The Silent Killers: 7 Examples of Mobile Device Security Risks
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Malware Families, Mobile Threats, and the Human Risk Narrative Shaping Cybersecurity
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.
.webp)

Securing Agentic AI on Mobile
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mobile App Security Assessment: Identifying Risks Before Attackers Do
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mobile Threat Defense: Penetration Testing Can Reveal Your Weakest Links
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Zero-Day Mobile Vulnerabilities: Why Speed is the Key to Cyber Defense
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Agentic and Generative AI: Differences and Impact on Organizational Growth
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Ethical and Regulatory Implications of Agentic AI: Balancing Innovation and Safety
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.



